
Introduction I could think of no better way to kick off 2022 than talking about one of the hottest buzzwords in Cyber Security today. Zero …
Guides and Designs for the Network Security Generalist

Introduction I could think of no better way to kick off 2022 than talking about one of the hottest buzzwords in Cyber Security today. Zero …

In the first part of this series, the explanation of how to configure the FortiAuthenticator with a BYOD guest portal was covered. In the second …

In the first part of this series, an overview of Bring Your Own Device (BYOD) with the FortiAuthenticator was covered. In addition to that, guidance …

When FortiAuthenticator is mentioned, what is the first thing that comes to mind? Most likely two-factor authentication, but maybe there is awareness around its ability …
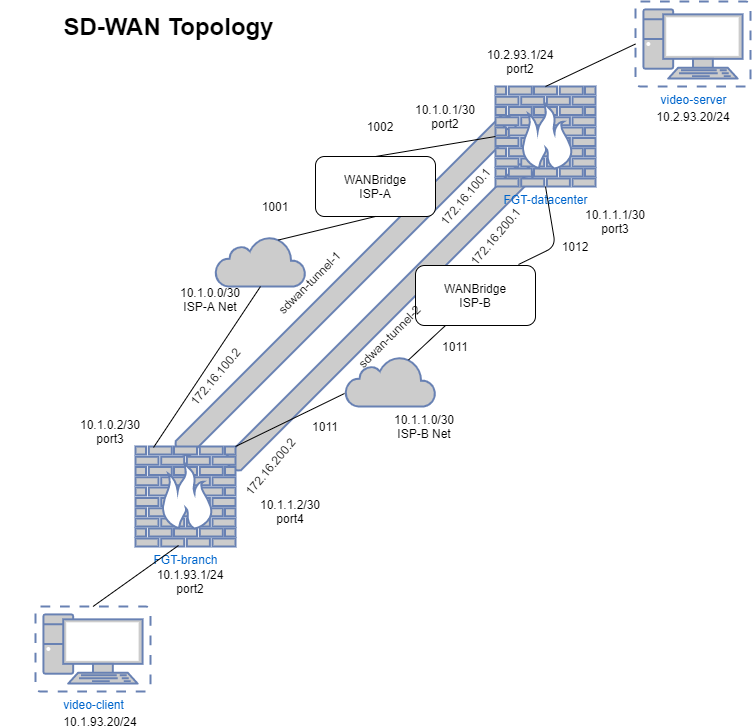
Introduction This previous article provides an overview of the FortiGate SD-WAN solution. This article will focus on the nuts and bolts of the actual configuration …

I know it has been a very long time since I have updated this blog but I blame it on 2020. At any rate, I …

Introduction Software Defined Wide Area Networking (SD-WAN) is a buzzword that seems to be here for the long haul. It carries the same longevity like …

This is the third (and final) installment in the three part series regarding managing FortiGate firewalls with the FortiManager. Please review the previous articles on …

This is the second installment of the three part series about using the FortiManager to manage the firewall policy of FortiGates. Review the first article …