In my previous post, I provided a brief overview of the importance of Zero Trust Network Access (ZTNA). Before I get into the nuts and bolts about how to configure ZTNA with the Fortinet solution, I first need to highlight a component that is super important but may not be top of mind when designing this solution. Domain Name Services (DNS) is typically critical in regards to any networking application but is especially paramount with this ZTNA design.
Importance of DNS
Before going into the specific application of DNS for ZTNA, I want to give a brief explanation of its importance. To illustrate this, I want to provide a real world example.
Back in the early 90s (wow, I am really predating myself), when I needed to call someone on the telephone, I had to recall their actual phone number to dial. It was quite the feat to remember a unique set of 10 digits for my house, my mom’s work and my dad’s work. Fast forward to today where if I need to call someone, I just pull them up on my contact list and select their name. I offload the responsibility for finding the actual number to my phone while I just have to remember the descriptive name to identify the contact.
DNS provids a very similar use case when a user wants to access a server/service on the Internet. The primary function of DNS is to allow a user to map a name (typically easier for a human to remember) to an IP address.
DNS in Fortinet Zero Trust Network Access
DNS serves two very important roles in the Fortinet Zero Trust Network Access solution. The first is that it allows for easy to remember access to the FortiClientEMS server for constant telemetry as well as the FortiGate which serves as the enforcement point for the access. This is key if you wish to expand your zero touch footprints and use DNS Load Balancing to choose a FortiGate ZTNA access gateway closest to your endpoint.
Secondly, DNS allows multiple to services to be accessible over a single port when the FortiGate is in “reverse proxy” mode since the FortiGate can choose a different back end server based on the domain name it receives from the client. This is indicated by all of these different domain names resolving to the same IP address in the screenshot below.
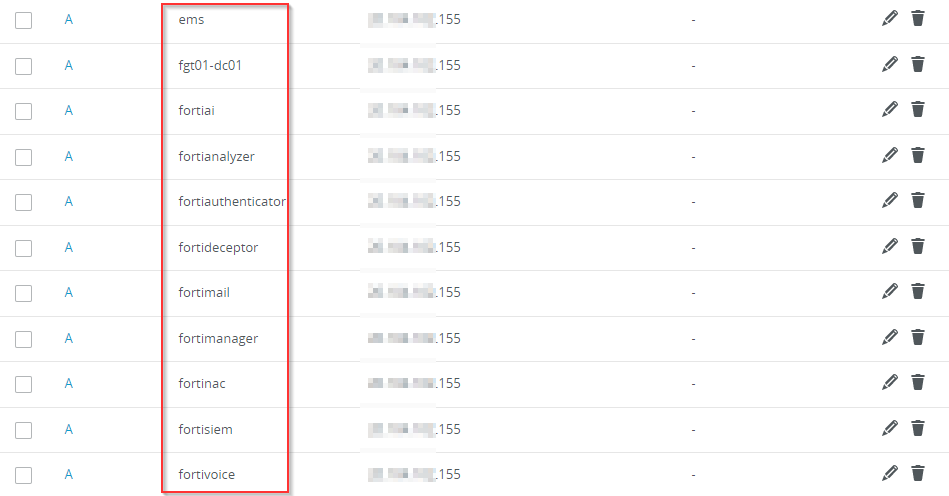
This allows for a single ZTNA access rule to be configured and allow multiple services to be accessible over a single port.
In the next series of blogs, I will go into more detail about how I configured the different components of the Fortinet ZTNA solution to provide secure remote access to my lab environment.
